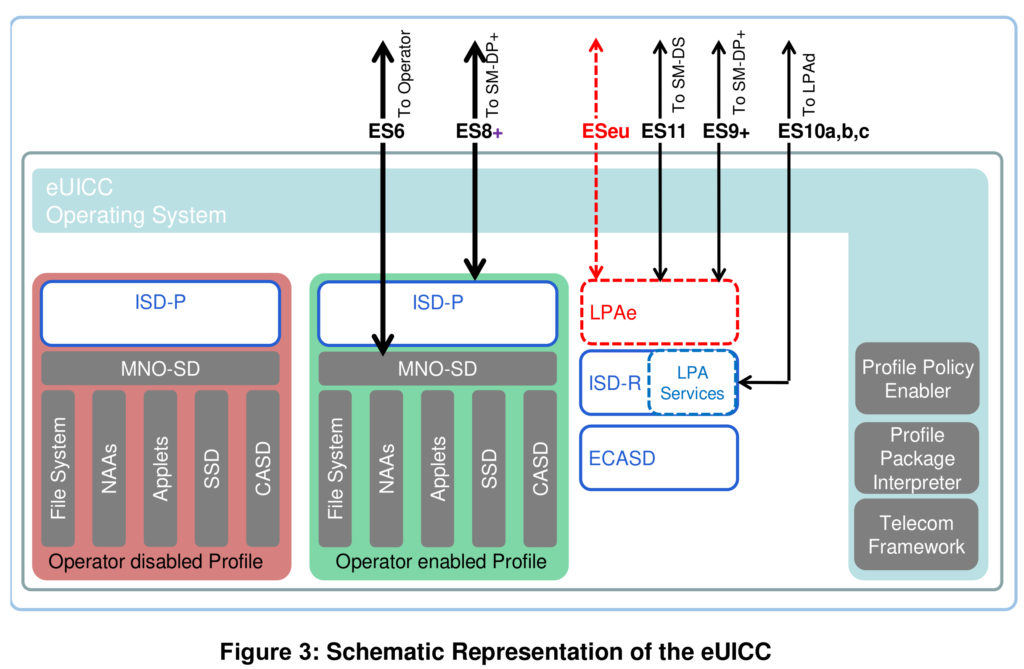
Embedded UICC Controlling Authority Security Domain (ECASD) 负责安全存储支持 eUICC 上所需安全域所需的凭证。
一个 eUICC 上应该只有一个 ECASD。 ECASD 应在 eUICC 制造期间由 EUM (卡商) 安装和个性化,如 GlobalPlatform 卡规范中所述。
ECASD 应包含以下内容:
1. 用于创建签名的 eUICC 私钥 eUICC’s Private Key(s) (SK.EUICC.SIG) 。
2. eUICC认证的证书 (CERT.EUICC.SIG), 此证书含有eUICC的公钥 (PK.EUICC.SIG)。
3. 用于验证 SM-DP+ 和 SM-DS 证书的证书颁发者 (CI) 根证书的公钥 (PK.CI.SIG) 。
4. eUICC 制造商 (EUM) 用于 更新 密钥/证书的密钥集 ((CERT.EUM.SIG)。
可以更新:
1)eUICC’s Private Key(s) 和 Certificate(s)
2) EUM Certificate(s)
3) eSIM CA RootCA public key(s)
4) 添加 新的 new eUICC Private Key(s), eUICC Certificate(s), EUM Certificate(s)
5)
此外,ECASD 应提供在密钥建立和 eUICC 身份验证期间使用的安全功能。
ISD-R 负责创建新的 ISD-P 和 管理 所有 ISD-P 的生命周期。
ISD-P 是用于托管 配置文件(Profile)的安全容器(安全域)。 ISD-P 与配置文件包解释器(用于对接收到的绑定配置文件包,进行解码/解释) 协作, 来完成配置文件下载和安装.
ISD-P是 SM-DP+ 在卡上的代表。
MNO-SD
MNO-SD 是发布配置文件的运营商的卡上代表。 它包含运营商的无线 (OTA) 密钥并提供安全的 OTA 通道。
Profile Policy Enabler
eUICC 操作系统 (OS) 的一个服务,提供配置文件策略规则验证和执行。
Telecom Framework
Telecom Framework 是一种操作系统服务,它为 ISD-P 中托管的 NAA(SIM卡应用) 提供标准化的网络认证算法。 此外,它还提供了使用必要参数配置算法的能力。
Profile Package 解释器是一个 eUICC 操作系统服务,它 将 Profile Package Data 转换为 目标 eUICC 的特定内部格式 的Profile.
LPA 服务
提供 对 (LPA功能要求中定义的)的服务和数据的访问,包括:
1. root SM-DS地址。
2. 可选存储的默认 SM-DP+ 地址。
3. 便于接收从 LPA 传输的绑定配置文件包。(从LPAd传到ISD-P)
4. 提供有关已安装配置文件及其配置文件元数据的信息。
5. 提供本地配置文件管理
6. 支持远程配置文件管理操作
7. 为LPA 提供与SM-DS 进行身份验证和交互的功能。
8. 确保对 EID 的访问仅限于 LPA。